Maintaining a secure website is crucial for protecting sensitive information and ensuring a seamless user experience. Unfortunately, cybercriminals frequently target websites, injecting malicious code and compromising websites.
In this article will guide you through identifying and removing viruses from your website using cPanel, helping you restore your site’s integrity and protect it from future threats.
By going through this article step-by-step, you will know how to scan your cPanel to detect and eliminate malware to ensure your websites remain secure and trustworthy. You may also see our expert step-by-step guide on how to get a cPanel (step-by-step guide).

One of the tools for managing websites is cPanel, in this way, attackers try to add malicious directories into the cpanel if they are trying to hack or spam a website.
When your website is hacked, it may not stop working. At times, a hacked website can be effectively running. The aim of hackers is different. Sometimes, some hackers only demand some of your website visitors to automatically visit their website, some hackers like to degrade the appearance of your website in search engine results (for example turning your website description and title on search engines into fictitious language that you have never written on your website).
The threat of website hacking is a very serious issue. Depending on the type of code that the hacker added to your cpanel, they may let your website send spamming emails, let all your indexed pages disappear completely, make the changes you make on your website not take effect, etc. That’s why it’s important to pay attention to the security of your cPanel account.
These hackers may add a directory to your cpanel, change the code in the directories, or delete a directory in your cpanel. Experts point out that weak passwords cause this, usage of untested plugins and themes on a website gives room for hackers. In this article, we are only going to show you how to remove malicious directories, edited directories, and errors in your cpanel that affect the smooth running of your websites.
Now, let’s get started.
How to delete malicious directories in your cPanel
To know the malicious directories in your cPanel that you should delete, you can use Virus Scanner in your cPanel. The guide below is how to do that.
#1. Login to your cPanel and locate the Virus scanner in the advanced section by scrolling or searching in the search bar.
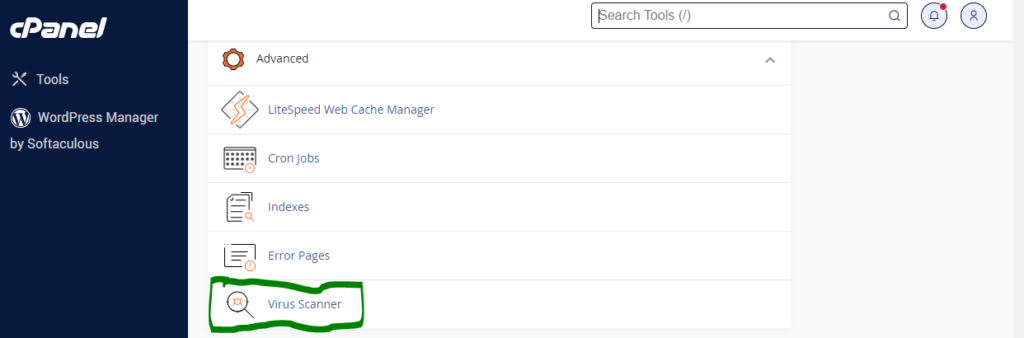
#2. Click the virus scanner button and select the entire home directory. Then click the scan now button.
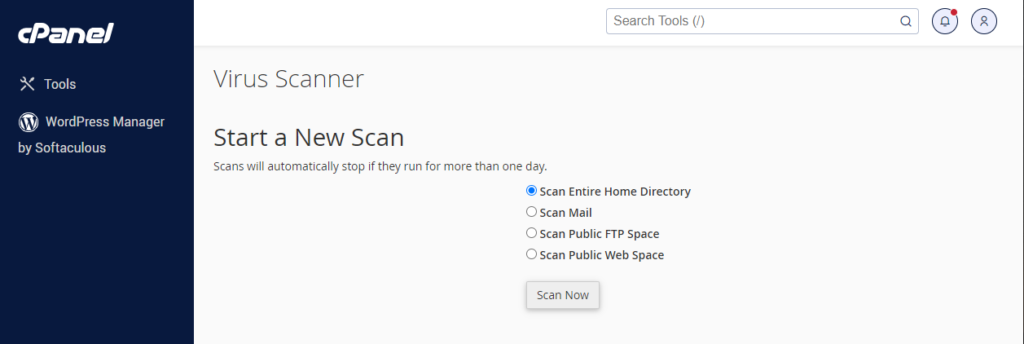
Wait for some time for the scanning to completely take place. While you are waiting, you can see the scanning report.
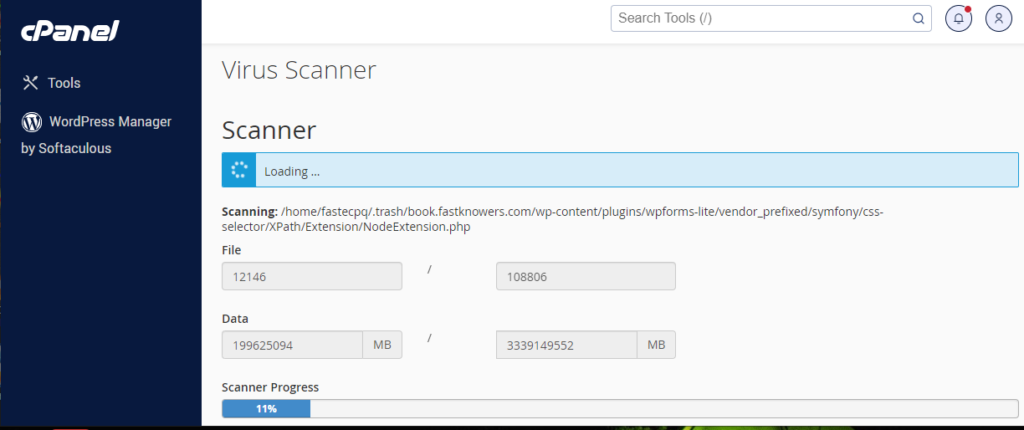
When the scanner progress reaches 100%, a successful notification below will be displayed. Click the close button.
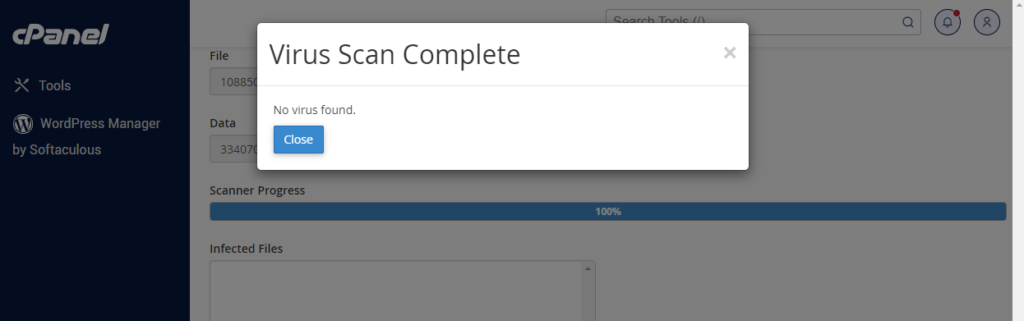
#3. After that, visit your cpanel and click the file manager button in the files section.
#4. Go to the /home/cPanel_username directory. The scan report is uploaded to it. Usually, its name contains your cPanel username and the date when the scanning was done, e.g., scanreport-nctest-Mar_17_2020_16h_53m.txt.
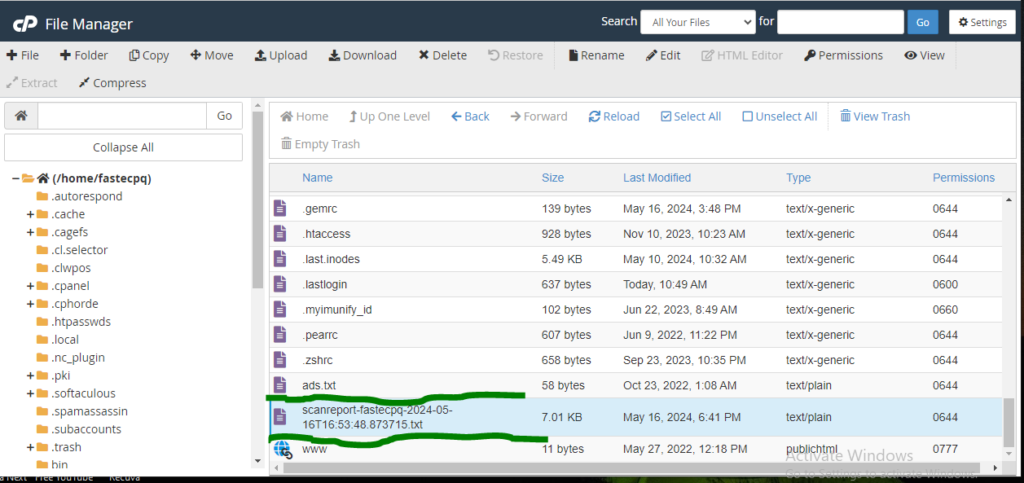
#5. Locate the file, right-click it, and click the Edit button.
Now, you can find all directories in your cpanel that are being corrupted or added by bots attackers, or hackers using this scanned report.
How to determine malicious directories in your cPanel
Below you can find malicious directories in the panel from the pasted text provided from our panel.
———– SCAN REPORT ———–
TimeStamp: Thu, 16 May 2024 12:53:50 -0400
(/usr/sbin/cxs –clamdsock /var/clamd –dbreport –defapache nobody –doptions Mv –exploitscan –nofallback –filemax 50000 –noforce –html –ignore /etc/cxs/cxs.ignore.manual –options mMOLfSGchexdnwZDRru –noprobability –qoptions Mv –report /home/fastecpq/scanreport-fastecpq-2024-05-16T16:53:48.873715.txt –sizemax 1000000 –ssl –summary –sversionscan –timemax 30 –nounofficial –user fastecpq –virusscan –vmrssmax 2000000 –waitscan 0 –xtra /etc/cxs/cxs.xtra.manual)
Scanning /home/fastecpq:
‘/home/fastecpq/.nc_plugin/hidden’
World writeable directory
Scan Timeout (30 secs) while processing:
‘/home/fastecpq/.trash/wordpress-6.5.2.zip’
‘/home/fastecpq/.trash/book.fastknowers.com/wp-content/plugins/astra-sites/astra-sites.php’
Script version check [OLD] [Starter Templates v4.2.2 < v4.2.3]
‘/home/fastecpq/.trash/book.fastknowers.com/wp-content/plugins/woocommerce/includes/admin/class-wc-admin-menus.php’
Universal decode regex match = [universal decoder]
‘/home/fastecpq/.trash/book.fastknowers.com/wp-content/plugins/woocommerce/src/Internal/Admin/WcPayWelcomePage.php’
Universal decode regex match = [universal decoder]
‘/home/fastecpq/.trash/book.fastknowers.com/wp-content/plugins/woocommerce/vendor/maxmind-db/reader/ext/maxminddb.c’
Suspicious file type [application/x-c]
‘/home/fastecpq/.trash/book.fastknowers.com/wp-content/themes/astra/admin/includes/class-astra-menu.php’
Universal decode regex match = [universal decoder]
‘/home/fastecpq/.trash/domain.fastknowers.com/wp-content/languages’
World writeable directory
‘/home/fastecpq/.trash/domain.fastknowers.com/wp-content/languages/plugins’
World writeable directory
‘/home/fastecpq/.trash/domain.fastknowers.com/wp-content/plugins/updraftplus/vendor/guzzle/guzzle/src/Guzzle/Service/Command/LocationVisitor/Request/admin.php’
Decode regex match = [decode regex: 1]
‘/home/fastecpq/.trash/domain.fastknowers.com/wp-content/themes/astra/admin/includes/class-astra-menu.php’
Universal decode regex match = [universal decoder]
‘/home/fastecpq/.trash/optimole-wp/vendor/codeinwp/themeisle-sdk/assets/js/build/tracking/class-add.php’
Known exploit = [Fingerprint Match (fp)] [PHP Exploit [P2226]]
‘/home/fastecpq/.trash/optimole-wp/vendor/codeinwp/themeisle-sdk/assets/js/build/tracking/random2.php’
Known exploit = [Fingerprint Match (fp)] [Hacker Sig Exploit [P2071]]
‘/home/fastecpq/.trash/optimole-wp/vendor/codeinwp/themeisle-sdk/assets/js/build/tracking/wp-ddd.php’
Known exploit = [Fingerprint Match (fp)] [PHP Exploit [P2226]]
‘/home/fastecpq/.trash/woocommerce/includes/admin/class-wc-admin-menus.php’
Universal decode regex match = [universal decoder]
‘/home/fastecpq/.trash/woocommerce/src/Internal/Admin/WcPayWelcomePage.php’
Universal decode regex match = [universal decoder]
‘/home/fastecpq/.trash/woocommerce/vendor/maxmind-db/reader/ext/maxminddb.c’
Suspicious file type [application/x-c]
‘/home/fastecpq/.trash/wp-live-chat-support/admin/class-wplc-plugin-settings.php’
Universal decode regex match = [universal decoder]
Scan Timeout (30 secs) while processing:
‘/home/fastecpq/public_html/old files/wordpress-6.0.zip’
‘/home/fastecpq/public_html/old files/wp-includes/version.php’
Script version check [OLD] [Wordpress v6.0.3 < v6.5.3]
‘/home/fastecpq/public_html/wp-content/plugins/ad-inserter/includes/google-api/vendor/phpseclib/phpseclib/phpseclib/Crypt/EC/Curves/sect571k1.php’
Universal decode regex match = [universal decoder]
‘/home/fastecpq/public_html/wp-content/plugins/ad-inserter/includes/google-api/vendor/phpseclib/phpseclib/phpseclib/Crypt/EC/Curves/sect571r1.php’
Universal decode regex match = [universal decoder]
‘/home/fastecpq/public_html/wp-content/plugins/ad-inserter/includes/google-api-8/vendor/phpseclib/phpseclib/phpseclib/Crypt/EC/Curves/sect571k1.php’
Universal decode regex match = [universal decoder]
‘/home/fastecpq/public_html/wp-content/plugins/ad-inserter/includes/google-api-8/vendor/phpseclib/phpseclib/phpseclib/Crypt/EC/Curves/sect571r1.php’
Universal decode regex match = [universal decoder]
‘/home/fastecpq/rakaalservices.com/wp-content/plugins/megamenu/classes/pages/page.php’
Universal decode regex match = [universal decoder]
‘/home/fastecpq/rakaalservices.com/wp-content/themes/astra/admin/includes/class-astra-menu.php’
Universal decode regex match = [universal decoder]
‘/home/fastecpq/rakaalservices.com/wp-content/themes/furnitrix/gard0.php’
Decode regex match = [decode regex: 1]
‘/home/fastecpq/rakaalservices.com/wp-content/wpvivid_uploads/Isolate/export.php’
Universal decode regex match = [universal decoder]
Decode regex match = [decode regex: 1]
‘/home/fastecpq/rehaadglobal.com/wp-content/plugins/astra-sites/astra-sites.php’
Script version check [OLD] [Starter Templates v4.2.2 < v4.2.3]
‘/home/fastecpq/rehaadglobal.com/wp-content/themes/astra/admin/includes/class-astra-menu.php’
Universal decode regex match = [universal decoder]
‘/home/fastecpq/shop.rakaalservices.com/wp-content/plugins/astra-sites/astra-sites.php’
Script version check [OLD] [Starter Templates v4.2.2 < v4.2.3]
‘/home/fastecpq/shop.rakaalservices.com/wp-content/plugins/header-footer-elementor/header-footer-elementor.php’
Script version check [OLD] [Elementor Header & Footer Builder v1.6.28 < v1.6.31]
‘/home/fastecpq/shop.rakaalservices.com/wp-content/plugins/megamenu/classes/pages/page.php’
Universal decode regex match = [universal decoder]
‘/home/fastecpq/shop.rakaalservices.com/wp-content/plugins/ultimate-addons-for-gutenberg/ultimate-addons-for-gutenberg.php’
Script version check [OLD] [Spectra v2.13.1 < v2.13.2]
‘/home/fastecpq/shop.rakaalservices.com/wp-content/plugins/ultimate-addons-for-gutenberg/admin-core/inc/admin-menu.php’
Universal decode regex match = [universal decoder]
‘/home/fastecpq/shop.rakaalservices.com/wp-content/plugins/ultimate-addons-for-gutenberg/includes/blocks/forms/frontend.css.php’
Universal decode regex match = [universal decoder]
‘/home/fastecpq/shop.rakaalservices.com/wp-content/plugins/woocommerce/includes/admin/class-wc-admin-menus.php’
Universal decode regex match = [universal decoder]
‘/home/fastecpq/shop.rakaalservices.com/wp-content/plugins/woocommerce/src/Internal/Admin/WcPayWelcomePage.php’
Universal decode regex match = [universal decoder]
‘/home/fastecpq/shop.rakaalservices.com/wp-content/plugins/woocommerce/vendor/maxmind-db/reader/ext/maxminddb.c’
Suspicious file type [application/x-c]
‘/home/fastecpq/shop.rakaalservices.com/wp-content/plugins/wp-live-chat-support/admin/class-wplc-plugin-settings.php’
Universal decode regex match = [universal decoder]
‘/home/fastecpq/shop.rakaalservices.com/wp-content/themes/astra/admin/includes/class-astra-menu.php’
Universal decode regex match = [universal decoder]
———– SCAN SUMMARY ———–
Scanned directories: 13920
Scanned files: 106893
Ignored items: 451
Suspicious matches: 40
Viruses found: 0
Fingerprint matches: 3
Data scanned: 3111.10 MB
Scan peak memory: 395788 kB
Scan time/item: 0.024 sec
Scan time: 2879.199 sec
Pay attention to the scanned report. It contains the following information:
- path to the directory or file (e.g. ‘/home/cPanel_username/public_html/vendor/laravel/framework/src/Illuminate/Filesystem/Filesystem.php’) ;
- scan result (e.g. # Regular expression match = [symlink\s*\(]).
Now that you have know the directories in your cpanel which are being corrupted, you need to delete them from your cpanel. Please read the table below. It will show you the directories in your scanned reports which you need to delete.
| Result | Description | Action to take |
|---|---|---|
| # ClamAV detected virus | Antivirus software has found a potentially dangerous file with malware. | Remove the file. |
| # Suspicious file type [application/x-c] # MS Windows Binary/Executable [application/x-winexec] # (compressed file: Moxie.dll [depth: 1]) MS Windows # Binary/Executable [application/x-winexec] # MS-DOS Binary/Executable [application/x-dosexec] | Antivirus software has found Windows binary or executable files. Such files cannot be executed on a Linux-based OS. You would not normally expect to find one within a cPanel account . You can discover a Trojan file among them. | Remove the file. |
| # Linux Binary/Executable [application/x-sharedlib] | Antivirus software has found Linux binary or executable files. Such files can be executed on a Linux-based OS. Still, you would not normally expect to find one within a cPanel account. If a Linux binary or executable file is located in a cPanel account, it is most likely an exploit that remains hidden. | Remove the file. |
| # Known exploit = [Fingerprint Match] | Antivirus software considers a file as an exploit. An exploit can be a program, a piece of code, or even just a string of characters. It takes advantage of a program. Then, this program acts in an unexpected way, which results in undesirable behavior. Also, exploits are maliciously used to gain unauthorized access. | Unless you know the purpose of this file, remove it from your cPanel. If it is related to installed software and you need it, either clean it or upload again from a trusted source. PLEASE NOTE: It is strongly recommended that you use content only from the official source. |
| # Symlink to | The file is a symbolic link. It consists of a special type of file that serves as a reference to another file or directory. Some default files require symlinks for the proper work of cPanel services: ‘/home/cPanel_username/.cagefs/opt/alt/phpXX/link/conf’ ‘/home/cPanel_username/access-logs’ ‘/home/cPanel_username/.cagefs/tmp/mysql.sock’ But the custom symlinks (e.g. a symlink to files outside of your cPanel account) may cause serious security breaches. | Pay attention to the custom symlinks. Such files should be removed from your account. Symlinks to default cPanel files can be ignored. |
| # Socket | A socket is typically used to transfer data between two separate processes. You would not expect to normally find one within a cPanel account. | Unless you know the purpose of this file or it is related to the software installed from the trusted source, remove it from your cPanel. |
| # Regular expression match = [symlink\s*\(] | A file contains ‘symlink(s)’ expression as a comment or variable. | It is a false-positive. The file can be ignored. |
| # Regular expression match = [\n(?!\s*(//|\#|\*)).*/etc/passwd] | A file contains ‘/etc/passwd’ expression as a comment or variable. | It is a false-positive. The file can be ignored. |
| # Regular expression match = [\n(?!\s*(//|\#|\*)).*\.ssh/] | A file contains ‘/.ssh’ expression as a comment or variable. Such files are potentially harmful to your account as they allow remote access using SSH keys. | Unless you know the purpose of this file or it is related to the software installed from the trusted source, remove it from your cPanel. |
| # Universal decode regex match | A file contains some string encoded with a common encoder, e.g. base64. They are often used to hide malicious code. | Unless you know the purpose of this file or it is related to the software installed from the trusted source, remove it from your cPanel. |
| # Script version check [OLD] | The installation, plugin or theme version is outdated. Software updates are important because they check for the bugs and vulnerabilities found in the previous versions. A ‘hole’ in one can affect your entire installation as well as your cPanel account. | Ensure that your installations are up to date. |
| # World writeable directory | Permissions for a directory are set to 777. It is recommended to have default permissions assigned to website files and folders. They are 644 for files and 755 for folders. However, it is safe to have permissions set to 777 for default cPanel folders: /home/cPanel_user/.cagefs/var/cache /home/cPanel_user/.cagefs/var/php /home/cPanel_user/.cagefs/var/run | Update permissions for the indicated directory. |
| # Scan Timeout (30 seconds) while processing | The scan process has been interrupted. | You can put in a request to our Support Team to scan it additionally. |
| # Clamd Error for | Antivirus software considers that the file is located inside the service directory, therefore, it should not be scanned. | The file can be ignored. |
Before you delete or edit any directory in your cpanel, please make sure to create a backup. Files with randomly-generated names (e.g. bcwfgi.php) always contain malicious code. Hence, they need to be deleted.
How to delete malicious directories in your cpanel
By now, you have known how to scan and determine malicious directories in your cpanel. The next guide now is showing you how to delete such directories from your cpanel. Watch the video above in full version here.
Now, let us get started.
#1. Login to your cpanel and click the file manager button.
#2. Scroll through your cpanel to meet the directory that you want to delete (e.g, ‘/home/fastecpq/rakaalservices.com/wp-content/themes/furnitrix/gard0.php’) as you have found out from your virus scanner report.
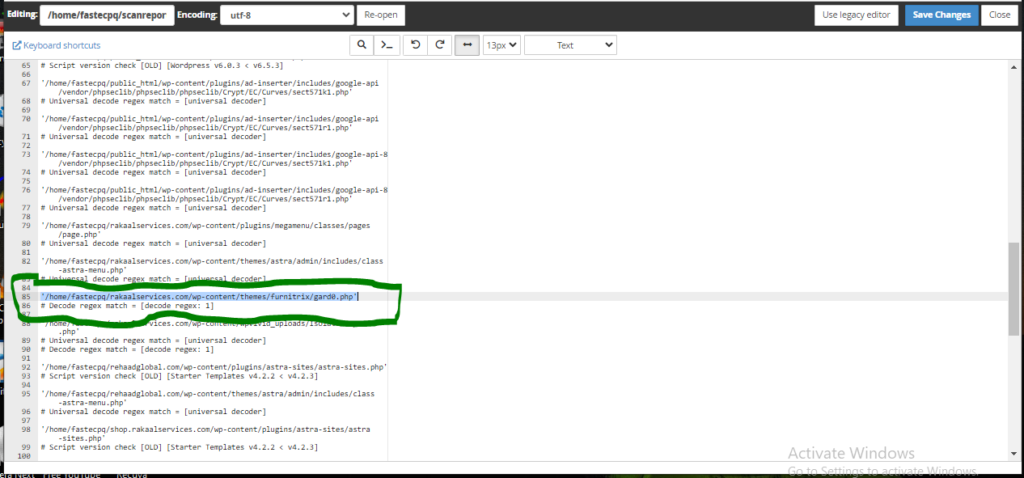
If we want to delete the directory in the screen shot above from our cPanel, first of all, we need to visit the home directory (fastecpq or username of the cpanel), then rakaalservices.com, wp-content, themes, furnitrix, and finally gard0.php.
Now, let begin.
#3. In your file manager, navigate to rakaalservices.com and double click it.
#4. Double click the wp-content.
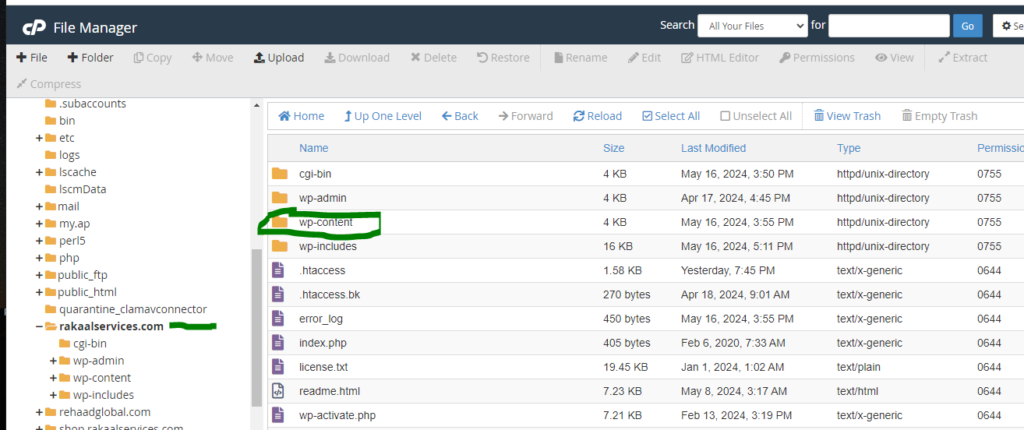
#5. Double themes
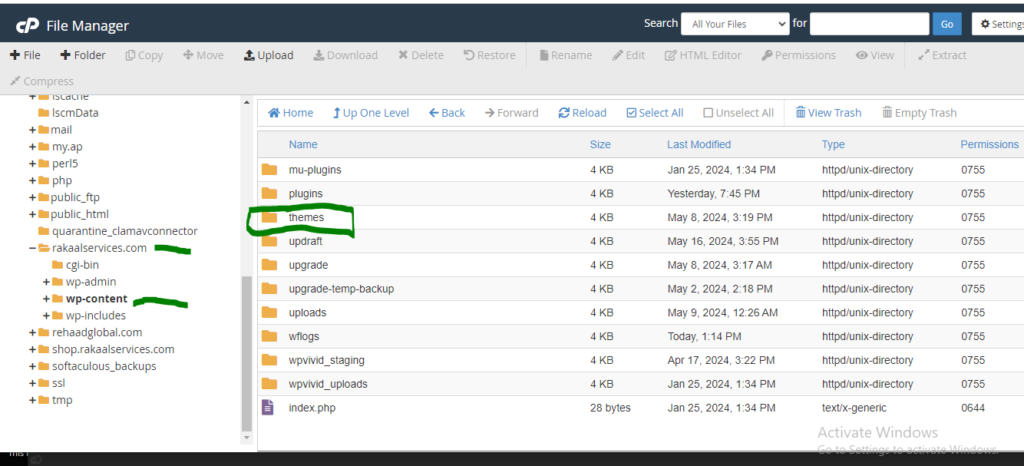
#6. Double click furnitrix
#7. Hover over on the gard0.php and click the delete button.
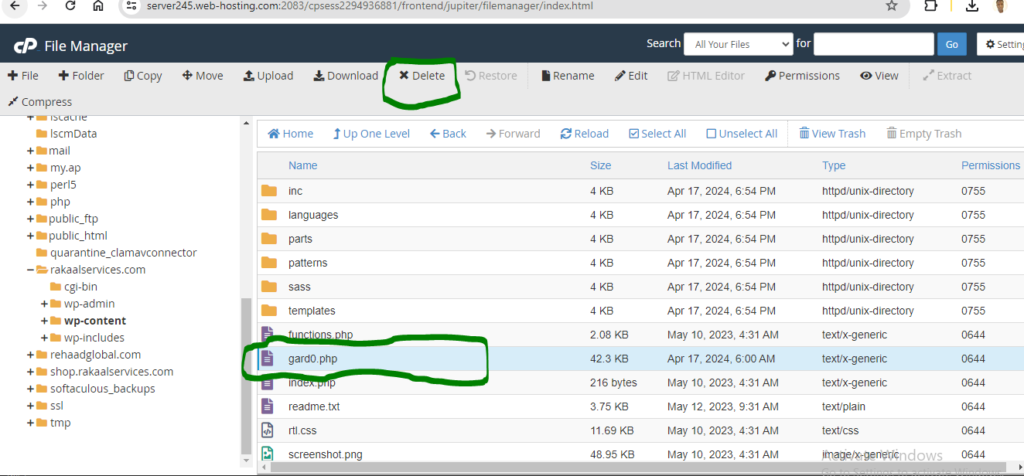
#8. Review the file and click the confirm button
Before you delete any file or directory from your cpanel, you will be notified to review your request first. They will also give you a chance to either select the skip the delete (trash) and permanently delete the trash. If you permanently delete it, you will can never restore it, but if you trash it, you can restore it and get your website back to the way it was incase the file is not the one you should delete.
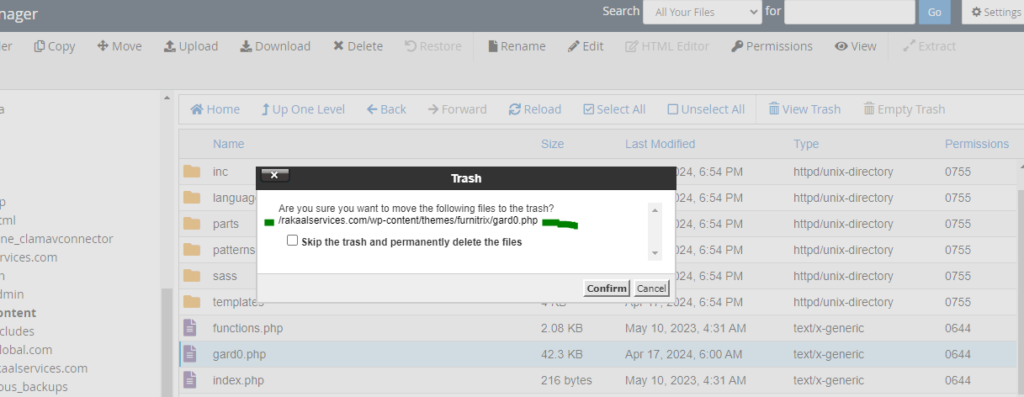
Please confirm the file in your virus scanner report to the one on the trashing confirmation section before you delete. In this guide, I hope we are correct. The file we want to delete is (/home/fastecpq/rakaalservices.com/wp-content/themes/furnitrix/gard0.php’) and the one that is showing is (/rakaalservices.com/wp-content/themes/furnitrix/gard0.php) which is the same. Thus, we can go ahead and delete it.
Conclusion
Hope this article has shown you the expert step-by-step guide on how to remove malicious errors, codes, files and directories from your website via cPanel. You may also watch the video below for guide.
If you know that this article has helped you, please share it with your friends. Subscribe to our YouTube channel if you haven’t subscribed yet. Could you be able to completely remove malicious files in your cPanel? Please let know via the comment box.






This article has enabled me to know virus scanner, a feature in my cPanel which I never knew it exists.
I have also used the guide in this article to know to scan website viruses and I have now accessed hacked files on my cPanel.
The problem that I am facing now is how to trace and delete those hacked files. As a result of that, I need help sir. Can I hire you or your team to help me? I am desperate 😩
This guide has helped me cleaned viruses from my website’s cPanel. Thank for managing this blog.
By the aid of this article, I could be able to find the virus scanner in my cPanel. And I have used it to make virus scan on my website’s cPanel. The next thing I need help with is how to know which code to delete and the one that should not be deleted. Please can you provide me with any help?
Thank you for this step-by-step guide. I value your help in this platform. I look forward to consuming your content. You are an amazing selfless web security specialist I have ever known. 😊
I am very happy as I could be able to use your guide to remove viruses from my cPanel. I have subscribed to your channel and newsletter already.
Glad you found the article helpful.